Things are not looking up for NSO Group, to say the least. It’s the world’s leading Black Hat cyber-security company. Its Pegasus malware is the most-advanced hacking tool in the world. It has been used by as many as 40 intelligence agencies, many working for repressive regimes, to seize control of cell phones belonging to human rights activists, journalists, teachers, and victims of state violence. For several years, the company was the darling of the cyber-security industry with valuations approaching $1-billion. When it finally sold itself to the UK venture capitalist, Stephen Peel of Novalpina Capital, the start-up founded by two floundering IDF veterans looking for the “next big thing,” had achieved magical unicorn status and became mega-wealthy overnight.
But in the process of shopping their company to major international investors, they discovered a certain level of toxicity in their business plan of selling Pegasus to some of the dirtiest, most oppressive governments the world has to offer. Two sets of buyers, one of whom was the powerful venture capital firm, Blackrock, announced a purchase only to back away after human rights groups like Access Now and others warned them off a business association with a company marketing pain and suffering to victims of state violence and their defenders. Verint similarly walked away from such a deal.
Peel, however, was undaunted. Being aware of the previous controversy, he announced with great fanfare that NSO would create a gold standard for ethical practice in its field. He hired expert consultants to create such guidelines. He trumpeted adherence to the United Nations Guiding Principles on Business and Human Rights as the goal of his efforts. Yet somehow, despite all the promises of turning over a new leaf, nothing changed.
Prior to buying NSO, Peel had burnished his reputation as a human rights activist by serving on the board of Global Witness. His wife, Jana, was the director of London’s Serpentine Gallery. Both were forced to resign their respective positions due to the fallout from their new ownership roles in the cyber-hacking enterprise.
The Guardian reports that NSO has been invited to a highly secretive cyber-weapons fair hosted by the UK Home Office annually. Unlike in past years, the company’s participation this year has aroused a storm of criticism, considering at least three British residents have been victims of Saudi Arabia hacking using Pegasus.
Khashoggi’s Murder ‘Ruined’ Everything
Then Jamal Khashoggi was assassinated by senior Saudi intelligence agents in Istanbul. The murder was carried out under the direct orders of the Crown Prince Mohammed bin Salman.

News reports had already noted that the Saudi intelligence agency had inked a $55-milion deal with NSO for the use of Pegasus, which the company claims is meant to fight terrorism and drug gangs (though it does not deny its use in the manner I’ve outlined here). Citizen Lab had already identified a number of hacks the Saudis had perpetrated using Pegasus. So suspicion immediately fell on NSO as being an accessory to the murder.
Citizen Lab had already documented that the cell phone of a close Khashoggi associate and fellow Saudi dissident, Omar Abdulaziz, had been hacked; and that the Saudis had access to the latter’s communications during the entire period when they were spying on him and preparing to execute Khashoggi. No news outlet has yet confirmed that the Saudis had hacked Khashoggi’s phone. But they wouldn’t necessarily have needed to if they had access to Abdulaziz’ and he was in close contact with the Washington Post journalist.
The Khashoggi murder marked a turning point both for Saudi relations with the west, which took a dramatic turn for the worse; and for NSO’s fortunes and reputation as well. After Amnesty International announced that NSO malware had targeted one of its staff members based in Geneva, the NGO filed the first lawsuit ever mounted against the company in Israel itself.
Within the past week, Reuters reported that the FBI itself was beginning an investigation of NSO. This was spurred by a referral made by Whatsapp itself to the Justice Department. One piece of blockbuster news was that the federal inquiry would cover the possibility that Pegasus had been used to hack the communications devices of U.S. government officials.
Sen. Ron Wyden had raised suspicions last November about NSO targeting Americans generally, and federal employees, specifically:
“If foreign surveillance companies like NSO are helping their foreign government customers hack or spy on Americans, particularly US government employees and contractors, that would raise serious national security issues,
He also expressed a suspicion that American citizens may be aiding NSO in this effort. If true, this would be an unprecedented development. It’s known that the company hires most of its employees from the ranks of the IDF Unit 8200, its much-vaunted SIGINT intelligence force. Until now, NSO has not admitted to hiring Americans, though a rival UAE firm, Dark Matter, has done this. In that case, the FBI also announced it was investigating whether the company or the American contractors had violated U.S. laws.
Though news that the Saudis used Pegasus to spy on U.S. officials would be an astonishing development if true, it shouldn’t surprise anyone since a repressive regime governed by an impetuous bully like Bin Salman would accept no constraints on its behavior.
Returning to the Amnesty Israel trial, it demanded that the Israeli defense ministry, whose export licensing unit approves the sale of all Israeli technology with security and military uses, revoke NSO’s license to export Pegasus. This would, in effect stop the company in its tracks and kill the goose that was laying the golden eggs.
The case is being heard in an Israeli court. The ministry has demanded that the trial be heard behind closed doors. Curiously, it hasn’t claimed that any national security secrets would be compromised. It merely argued to the judge that if the public heard the arguments advanced by Amnesty’s lawyers against NSO that it might persuade the public to believe they were true. That is one of the oddest arguments I’ve ever heard for slapping a secrecy order on judicial proceedings. The judge, of course, agreed and the case is now under seal. This significantly eases the burden on NSO and the defense ministry. Now neither the arguments nor the rulings of the judge are subject to public scrutiny. As with much of what happens in the Israeli national security state, secrecy protects the perpetrators of crimes committed in the name of the Israeli people.
A few months ago, another cyber-security company announced that it had detected a vulnerability in Facebook’s Whatsapp product which had permitted a nation-state to compromise the phones of 1,400 victims it targeted. Once again, the country was identified as Saudi Arabia and the malware used attributed to NSO. This has led to yet another lawsuit filed by Facebook against NSO. This one in U.S. federal court.
NSO: Ethics-washing and the Co-Optation of Ex-Obama National Security Officials
Though the company is by no means on its last legs, it is definitely on the defensive. A further example is the resignation of one of the ethics consultants it hired, Juliette Kayyem. She is a lecturer at the Belfer School at Harvard and a former Obama administration national security official. She boasted that her role as senior advisor would be to implement the highest ethical standards for NSO and its products. However, she never made clear just what she did, what she recommended, or what the company adopted in order to enforce these supposed principles. Presumably, she was involved in the writing of these so-called human rights guidelines adopted by the company.
Last year NSO hired law firms Paul Hastings and Paul, Weiss, Rifkind, Wharton & Garrison to give its so-called ethics guidelines legal cover:
Former Homeland Security Secretary Jeh Johnson wrote on behalf of Paul Weiss that the firm’s “proposed new Human Rights Policy and attendant governance documents of the Group are substantially aligned” with the United Nations Guiding Principles on Business and Human Rights.
It is certainly no coincidence that Johnson was Kayyem’s boss at DHS, when both worked there during the Obama administration.
This week, Harvard had planned to host a seminar for female journalists regarding online harassment and how to confront it. Kayyem was to be one of the two presenters. However, the journalists themselves began to ask how someone consulting for a company whose products target, and physically endanger journalists, could teach female reporters how to protect themselves from harassment. Yesterday, the Shorenstein Center announced the cancellation of the webinar. And today, the Guardian reported that Kayyem had stepped down from her role with the company.
This wasn’t the first time that she had faced controversy for her consulting role with the Israeli company. Several months ago, the Washington Post announced that she would become a regular contributor to its Opinion section. Critics immediately noted the discordance of the Post hiring a columnist working on behalf of the cyber-hacking firm which was an accessory to the murder of Khashoggi, who himself was a Post contributor. She quickly announced that she would not be writing for the Post after all.
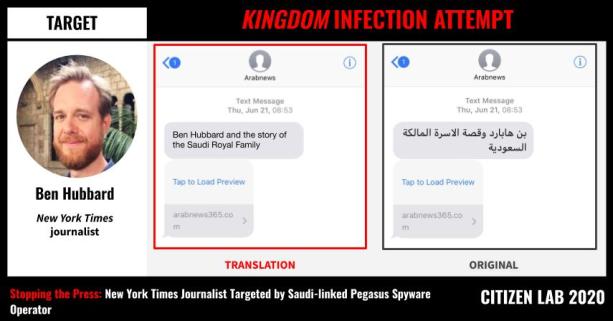
A First: MBS’s Failed Hack Against NY Times Journalist
A few days ago, NY Times Beirut bureau chief, Ben Hubbard, wrote that months earlier he had been targeted by Pegasus via an email. He had wisely not opened the message, which would have immediately downloaded the contents of his phone and offered the attackers access to everything he did, said or wrote subsequently. Hubbard sent his phone to Citizen Lab, which examined the phishing message and detected the server which would have connected to Hubbard’s phone had he clicked the link. The NGO determined that the server belonged to a network created by Saudi intelligence to target multiple victims. Hubbard holds the distinction of being the first U.S. journalist targeted by the Saudis using Pegasus.
While in the past, NSO refused to directly comment on any claims regarding its products targeting specific victims, it has launched into attack mode of late. When Hubbard asked NSO whether Pegasus had been used in the attempted hack, it denied it. But when the Times journalist reported the story, the Israeli company claimed that it had worked closely with Hubbard in investigating the incident and it falsely inferred that it had had access to his phone in doing so. This was meant to bolster its claim of innocence. However, Hubbard noted that he had only sent the company a screenshot of the message and link. Thus NSO could not possibly have claimed based on such evidence that Pegasus was not involved.

There is a further irony in the firm’s claim in this case. In the past, in order to evade any liability for damage caused to victims of its malware, NSO has claimed that it does not monitor uses of its products by clients. It supposedly tells them what purposes Pegasus should be used for and sends them on their merry way. It has also claimed that it could not monitor the use of the product even if it wanted to–a claim I flatly disbelieve.
So the question arises, if you cannot monitor how your product is used by your client how can you say for certain it wasn’t used in a particular hacking incident? You can’t, unless you go directly to the suspected client and ask them to tell you whether they were responsible. How many people in their right minds believe NSO would go to the Saudis and ask such a question? And how many believe even if it did, that the Saudis would tell them? Anyone who believes either is possible should contact me about some lovely beachfront property I want to sell you…in the swamps of central Florida.
NSO Media Offensive Smears Khashoggi’s Dissident Colleague
NSO has also gone on the offensive in its Israeli trial. It leaked vague and outrageous accusations against the Saudi dissident, Abdelaziz, who lives in exile in Canada. Based surely on information passed on to them by Saudi intelligence, a NSO source leaked to Ynet an unsourced claim that he had “published articles and tweets filled with hate, which called for violence.” Presumably the “violence” was to be directed against MBS himself, but the reporter doesn’t even specify this, let alone provide evidence of the substance of the claim with quotes or references to the original source. The report continues that the Saudi dissident has “sworn allegiance to ISIS” and that he supports BDS (!), again offering no proof. The irony of this of course is that the Saudi government provided the financial and military support for ISIS in Syria for years.
Ynet’s whispering campaign also includes the unsupported claim that he receives financial support from unnamed Arab countries “which support terror.” This seems to be a reference to Qatar, a Saudi bete noire. I have read a great deal about Abdulaziz, and never once heard such a claim. And even if true, Qatar’s sins regarding supporting terrorism are dwarfed by those of MBS, who has rained death and destruction on Yemen for years, and served as the major financier of ISIS in Syria.
In a company-wide memo, CEO Shalev Hulio expressed mock outrage against unspoken “hostile organizations” (presumably Citizens Lab) acting against us as part of a broader agenda, whose goal is to damage the company, as well as the State of Israel itself.” This line of argument is extremely popular in paranoid, ultra-nationalist Israel, where which human rights NGOs, whether foreign or domestic, are viewed as traitors to the nation. Hulio labors under the delusion that his company and the State itself are indivisible. An injury to him is an injury to the entire nation. Reminds you of another major narcissist stalking the halls these days, doesn’t it?
NSO pursued a similar line of attack when it hired another Israeli dirty-ops firm, Black Cube, to infiltrate Citizen Lab. A retired Israeli defense ministry employee assumed the identity of a fake cyber-security analyst seeking to pay the NGO’s researchers to deliver lectures at a non-existent conference. In this guise, he invited them to an elegant lunch near their Toronto offices. But instead of discussing the conference, he plied them with questions about Israel and whether they harbored hostile feeling toward it or supported the Palestinian cause. At this point, the Citizen Lab lunch guests knew there was something wrong with the situation. Of course, they harbored no particular feelings toward Israel or the Palestinians, and their only mission was to combat the sorts of cyber-weapons both Black Cube and NSO touted.
Returning to Hulio’s memo, in high dudgeon, he told employees that the company’s enemies had “crossed a red line” in their mounting attacks and that he would no longer stand by and watch as it became “an international punching bag.” The memo added that NSO had hired a major U.S. law firm to fight accusations against it in the U.S. The goal was, he wrote, to take NSO’s case to the United Nations and U.S. security agencies in order to clear its name of wrongdoing. He seems to be referring somewhat obliquely to charges by a UN official blaming Pegasus and Saudi Arabia for the hack of Jeff Bezos phone, which resulted in compromising photographs being published by the National Inquirer. The reference to U.S. security agencies may refer to the FBI investigation against NSO.
If you read Hebrew, Israeli media watchdog, 7th Eye, published an terrific evisceration of the Ynet article.
Another part of the company’s new offensive strategy involves the hiring of former Israeli chief military censor Brig. Gen. Ariella Ben Avraham. She is the iron-willed figure responsible for ensuring Israelis don’t learn secrets that would embarrass the IDF. She similarly, in her new role will be seeking to prevent the world from learning about the worst excesses by the company’s clients, which involve covering up its culpability for the long prison sentences and even death, suffered by victims.
NSO Brings in the Big Guns to Lobby Against Federal Criminal Investigation
Al Monitor reports that the Israeli company in fact hired several U.S. companies to lobby on its behalf. The most recent is Mercury Public Affairs, to whom it paid $1.4-million:
…For providing “strategic consulting and management services specific to government relations and crisis management issues” that Q Cyber faces in connection with “pending” and “potential future litigation or regulatory actions.” The firm also wrote…that it is providing “consulting services in connection with public relations, media relations, government relations, and litigation.”
One of the two individuals listed as working on the account once served as spokesperson the Justice Department Criminal Division. This indicates that NSO expects to be dealing with major federal criminal investigations.
Mercury was also implicated in the Mueller investigation for representing Paul Manafort. Unlike the Podesta Group which also worked for him and imploded as a result, Mercury came out relatively unscathed. The company also has contracted to lobby for the Turkish government. Though it claims to be a bipartisan shop, most of its staff have worked in or for Republican administrations and candidates.
The reason the Crown Prince has great interest in Ben Hubbard is that he’s writing critical pieces about him in one of the world’s most distinguished newspapers. Even more importantly, Hubbard has completed a book about MBS (see Amazon ad) which is due for publication in March. That will be a great month for book launches, as Bolton’s book will come out then as well.
The Saudi ruler-designate seeks to control everything said about him, whether newspaper columns or books. He can do that easily inside the Kingdom through the use of goons who enforce a code of silence on critics. Outside is a different story. But he’s made the mistake of believing he can use the same repressive, thuggish methods abroad as he does at home.
Targeting a NY Times journalist and killing another U.S. based journalist may have been a bridge too far for federal law enforcement. Though the Trump-Barr Justice Department has shown no interest in holding MBS to account, NSO is a different story. It doesn’t order tens of billions worth of military hardware from U.S. weapons manufacturers. It doesn’t hold half the world’s oil wealth. Thus it becomes a more vulnerable target.








Thx for the rant … very inquisitive! 😊
Global Targeting in Saudi Arabia – Iran religious conflict:
Some push-back by the Danes.
Three Iranian-Arab separatists have been under arrest in Denmark for the Ahvaz terror attack of 2018 in Iran. The prosecutor have added alleged espionage from 2012 -2018 for Saudi intelligence. Both in Denmark and in The Netherlands, the Saudi ambassador has been summoned to receive a diplomatic dressing down.
The Dutch had taken in hiding a long sought terrorist accused of the deadliest bombing in Tehran of 1981 killing top leaders and Ayatollah Behesti. Iran located the terrorist in Amsterdam after 35 years and liquidated him. A price was put on his head and a Moroccan mob under leadership of Ridouan Taghi took the contract. Taghi had been hiding in Dubai where he recently was arrested and extradited. The Dutch prosecution made serious work to find Taghi and his associates only after a lawyer Derk Wiersum was targeted and liquidated by the mob.
Targeting the poor through AI
Welfare surveillance system violates EU human rights law, Dutch court rules
Watched an interview by Adriaan van Dis recently: Yuval Noah Harari … historian and futurist, very interesting. New colonialism through twenty biggest tech corporations. Do forget about humanity and human rights from now on. The new normal …
With ‘The Dissident,’ Director Bryan Fogel Aims To Bring Justice To Murdered Freedom Fighter Jamal Khashoggi — Sundance Studio
https://deadline.com/video/the-dissident-director-bryan-fogel-sundance-studio-documentary-interview-news/
I question whether NSO software is “targeting Americans generally, and federal employees, specifically”.
NSO claims of it’s Pegasus software, that “…the product is specifically designed to not operate in the U.S.”
Citizen Lab makes the broad assertion, that cross-border targeting with Pegasus is “relatively common.”
but Citizen Lab hasn’t directly said that NSO software has been used to target Americans.
“We have identified several possible Pegasus customers not linked to the United States, but with infections in U.S. IP space,” Citizen Lab reports. “While some of these infections may reflect usage of out-of-country VPN or satellite Internet service by targets, it is possible that several countries may be actively violating United States law by penetrating devices located within the U.S.”
@ Lemontree: We have a choice to believe you and NSO or the FBI, Citizens Lab, and Sen. Ron Wyden. Gee, that’s not a hard choice to make.
As for targeting “Americans,” clearly the Saudis using Pegasus did target Ben Hubbard. So that argument goes out the window.
Also, the claim that Pegasus is designed not to operate in the U.S. is beyond ridiculous. First, I think you or whoever you quoted meant to say it’s not designed to work on U.S. telephone numbers. That is the excuse they used claiming they couldn’t have hacked Jeff Bezos. But either explanation is completely ridiculous. And even NSO designs Pegasus not to work in the U.S. or on U.S. phone numbers, I’ll bet there are many ways it could be modified by an NSO client to circumvent any such limitation. And I’ll bet NSO would be more than happy to look the other way if MBS and his crony-thugs did so.
Not only that, but Pegasus or other NSO tools were used to hack Whatsapp, an American company. And further, there may be Americans working for NSO who are offering it the means to penetrate the security of U. S. communications companies like Whatsapp. Sounds like a perfect storm of attack on U. S. Citizens and companies. And that’s why NSO is in deep shit and likely embroiled in federal criminal probes and lawsuits for years to come.
Britain of Conservative Boris Johnson post-Brexit and Israel’s NSO Group form a perfect pair …
UK to host spyware firm accused of aiding human rights abuses | The Guardian |
“Britain is OPEN for Business.”
Richard.
Why do you assume that Israeli software was involved in tracking Khashoggi, when the Saudis could just as easily have been using Italian, Hacking Team software?
https://www.washingtonpost.com/opinions/global-opinions/how-a-chilling-saudi-cyberwar-ensnared-jamal-khashoggi/2018/12/07/f5f048fe-f975-11e8-8c9a-860ce2a8148f_story.html
@ Lemontree: Didn’t you bother to read my post before writing your comment? If not, read the entire post before commenting and save me having to repeat the obvious. First, your article is nearly 2 yrs old.
A lot has changed in that time. Second, the Saudis used Pegasus to hack Abdulaziz. The latter was one of Khashoggi’s closest confidantes. Why would they use Pegasus to hack one of them and an entirely different product to hack the other? Doesn’t make sense.
Not to mention that the Saudi intelligence also used Pegasus to hack other Saudi dissidents. Whatever business MBS is doing with Hacking Team, Citizen Lab has never mentioned it in connection with any of the forensic examinations it’s done for Saudi hacking victims. It’s only discovered Pegasus, and multiple times.
Isn’t it curious that Ignatius’ column doesn’t mention Pegasus or NSO Group at all, when MBS signed a $55-million contract with the Israelis? Why might that be?
You apologists for Israeli cyber-thugs do have to step up your game!